网络安全实验报告书


姓名: 白晨
班级: 软件22
指导老师: 田暄
提交日期: 20##-12-10

目录
1 加解密与认证............................................................................................................................................... 2
1.1 实验环境................................................................................................................................. 2
1.2 源代码与注释........................................................................................................................ 2
1.3 运行结果与分析................................................................................................................... 7
2 RC4流密码加密实现................................................................................................................................. 8
2.1 实验环境................................................................................................................................. 8
2.2 源代码与注释........................................................................................................................ 8
2.3 运行结果与分析................................................................................................................ 10
3 大于3人实现证书生成、签发、通信.............................................................................................. 11
3.1 实验环境.............................................................................................................................. 11
3.2 实验过程与分析................................................................................................................ 11
1 加解密与认证
要求:结合所提供密码学开发库或利用Java,vc 自带密码学开发库完成如下要求
1)设计实现消息的机密性,完整性与可鉴别,认证要求。
2)报告中要有思路分析,设计流程与关键代码。每步变换后的结果
3)要求结合个人信息进行,如消息中应包含个人学号,姓名等
4)应使用到消息分组,不能太短
1.1 实验环境
语言 : Java
IDE : Eclipse绿色版
1.2 源代码与注释
import java.security.InvalidKeyException;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
import java.security.PrivateKey;
import java.security.PublicKey;
import java.security.SecureRandom;
import java.security.Signature;
import java.security.SignatureException;
import javax.crypto.BadPaddingException;
import javax.crypto.Cipher;
import javax.crypto.IllegalBlockSizeException;
import javax.crypto.KeyGenerator;
import javax.crypto.NoSuchPaddingException;
import javax.crypto.SecretKey;
publicclass EncryptionAndDecryption {
privatestaticfinalintGROUP_SIZE = 128;
privatestaticfinalintGROUP_MSG_SIZE = 28; // 28 bytes per group
privatestaticfinalintGROUP_HEAD_SIZE = 24;
privatestaticfinalintDIGEST_SIZE = 20;
privatestaticfinalintOFFSET_GROUP_SIZE = 20;
privatestaticfinalintOFFSET_CUR_GROUP = 22;
privatestaticfinalintOFFSET_MSG_START = 24;
privatestaticfinalintOFFSET_SIGN_SIZE = 77;
privatestaticfinalintOFFSET_SIGN_START = 78;
// Store plaintext
/* Attributes ***********************************************/
private String mMsg;
privatebyte[][] mCipers;
private MessageDigest mMsgDigest;
private KeyPairGenerator mKeyPairGenerator;
private PublicKey mPublicKey;
private PrivateKey mPrivateKey;
private Signature mSignature;
private KeyGenerator mKeyGenerator;
private SecretKey mDesKey;
private Cipher mCipher;
/* Encryption and Decryption *************************************/
public EncryptionAndDecryption() {
try {
mMsgDigest = MessageDigest.getInstance("SHA-1"); //Use SHA-1 to get Msgdigest
mKeyPairGenerator = KeyPairGenerator.getInstance("DSA");
// Signature Algorithm is DSA
SecureRandom secrand = new SecureRandom(); // Random
secrand.setSeed("BC".getBytes()); // Use bytes of text to generate a seed
mKeyPairGenerator.initialize(512, secrand);
// Generate the key pair
KeyPair keys = mKeyPairGenerator.generateKeyPair(); // Get keys
mPublicKey = keys.getPublic(); // Kpu
mPrivateKey = keys.getPrivate(); // Kpr
mSignature = Signature.getInstance("DSA");
mKeyGenerator = KeyGenerator.getInstance("DES"); // Encryption Algorithm
mDesKey = mKeyGenerator.generateKey(); // DesKey
mCipher = Cipher.getInstance("DES"); // Cipher
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
} catch (NoSuchPaddingException e) {
e.printStackTrace();
}
}
/**
* Split the message into group (28bytes per group)
* @return the message groups
*/
privatebyte[][] splitMsg() {
finalint groupSize = (mMsg.length()*2+1) / GROUP_MSG_SIZE + 1;
// System.out.println(groupSize);
// System.out.println(mMsg.length());
byte[][] msgs = newbyte[groupSize][GROUP_MSG_SIZE];
byte[] msgBytes = mMsg.getBytes();
//System.out.println(msgBytes.length);
for (int i = 0; i < groupSize; i++) {
for (int j = 0; (j < GROUP_MSG_SIZE) && (i * GROUP_MSG_SIZE + j < msgBytes.length); j++) {
msgs[i][j] = msgBytes[i * GROUP_MSG_SIZE + j];
}
}
return msgs;
}
/**
* Encryption
* @return Cipher
*/
publicbyte[][] encrypt() {
// Split the plain text into group
byte[][] plains = splitMsg(); // Plain text group
//System.out.println(plains.length);
//System.out.println(mMsg.length());
print(plains);
byte[][] groups = newbyte[plains.length][GROUP_SIZE]; // Message before encryption
byte[][] ciphers = newbyte[plains.length][]; // Message after encryption
// Encrypt the groups
for (int i = 0; i < groups.length; i++) {
// Msg digest
mMsgDigest.update(plains[i].clone());
byte[] digest = mMsgDigest.digest();
// Sign the message
byte[] signs = newbyte[0];
try {
mSignature.initSign(mPrivateKey);
mSignature.update(digest);
signs = mSignature.sign();
} catch (SignatureException e) {
e.printStackTrace();
} catch (InvalidKeyException e) {
e.printStackTrace();
}
// Fill digest
for(int j = 0; j < DIGEST_SIZE; j++) {
groups[i][j] = digest[j];
}
// Fill signature information
groups[i][OFFSET_SIGN_SIZE] = (byte) signs.length;
for (int s = 0; s < signs.length; s++) {
groups[i][OFFSET_SIGN_START + s] = signs[s];
}
// Fill the information of current group
byte[] groupSize = toByteArray(plains.length, 2);
groups[i][OFFSET_GROUP_SIZE] = groupSize[0];
groups[i][OFFSET_GROUP_SIZE + 1] = groupSize[1];
byte[] curGroup = toByteArray(i, 2);
groups[i][OFFSET_CUR_GROUP] = curGroup[0];
groups[i][OFFSET_CUR_GROUP + 1] = curGroup[1];
// Fill the message
for(int m = 0; m < GROUP_MSG_SIZE && m < plains[i].length; m++) {
groups[i][OFFSET_MSG_START + m] = plains[i][m];
}
// Print groups datum
System.out.println("");
for(byte[] temp : groups)
{
for(byte t: temp)
{
System.out.print(t + " ");
}
System.out.println();
}
// Encrypt the message
try {
mCipher.init(Cipher.ENCRYPT_MODE, mDesKey);
ciphers[i] = mCipher.doFinal(groups[i]);
} catch (IllegalBlockSizeException e) {
e.printStackTrace();
} catch (BadPaddingException e) {
e.printStackTrace();
} catch (InvalidKeyException e) {
e.printStackTrace();
}
}
return ciphers;
}
privatebyte[] toByteArray(int value, int i) {
// TODO Auto-generated method stub
byte[] b = newbyte[i];
b[1] = (byte) ((value>>8) & 0xFF);
b[0] = (byte) (value & 0xFF);
return b;
}
publicvoid setMsg(String msg) {
mMsg = msg;
}
publicvoid setCiphers(byte[][] ciphers) {
mCipers = ciphers;
}
publicbyte[][] decrypt() {
byte[][] plains = newbyte[mCipers.length][GROUP_MSG_SIZE];
byte[][] groups = newbyte[mCipers.length][GROUP_SIZE];
for (int i = 0; i < mCipers.length; i++) {
// Decryt the message group
byte[] plain = newbyte[GROUP_SIZE];
try {
mCipher.init(Cipher.DECRYPT_MODE, mDesKey);
plain = mCipher.doFinal(mCipers[i]);
} catch (InvalidKeyException e) {
e.printStackTrace();
} catch (IllegalBlockSizeException e) {
e.printStackTrace();
} catch (BadPaddingException e) {
e.printStackTrace();
}
// Verify the signature
byte[] signs = newbyte[plain[OFFSET_SIGN_SIZE]];
byte[] digest = newbyte[DIGEST_SIZE];
// Retrieve the digest
for (int d = 0; d < DIGEST_SIZE; d++) {
digest[d] = plain[d];
}
// Retrieve the signs
for (int s = 0; s < signs.length; s++) {
signs[s] = plain[OFFSET_SIGN_START + s];
}
try {
mSignature.initVerify(mPublicKey);
mSignature.update(digest);
if (mSignature.verify(signs)) {
// Verify the integrity
mMsgDigest.update(plain, OFFSET_MSG_START, GROUP_MSG_SIZE);
if(MessageDigest.isEqual(digest, mMsgDigest.digest())) {
// Get current group offset
byte[] curGroup = newbyte[2];
curGroup[0] = plain[OFFSET_CUR_GROUP];
curGroup[1] = plain[OFFSET_CUR_GROUP + 1];
int curPos = toInt(curGroup);
for (int j = 0; j < GROUP_MSG_SIZE; j++) {
plains[curPos][j] = plain[OFFSET_MSG_START + j];
}
}
};
} catch (SignatureException e) {
e.printStackTrace();
} catch (InvalidKeyException e) {
e.printStackTrace();
}
}
return plains;
}
publicstaticvoid print(byte plains[][]){
byte[] b = newbyte[(plains.length-1)*GROUP_MSG_SIZE+plains[plains.length-1].length];
int j=0;
int k=0;
for(int i=0;i<b.length;i++){
b[i] = plains[k][j];
j++;
if(j==plains[0].length){
k++;
j=0;
}
}
System.out.println(new String(b));
}
publicint toInt(byte[] b){
int value;
value = (int) ((b[0] & 0xFF)
| ((b[1] & 0xFF)>>8)
);
return value;
}
publicstaticvoid main(String[] args) {
EncryptionAndDecryption test = new EncryptionAndDecryption();
test.setMsg("白晨-2121601027-软件学院-软件22-网安实验-加密与解密");
test.setCiphers(test.encrypt());
print(test.decrypt());
}
}
1.3 运行结果与分析

实验所用加密算法为 DES, 签名算法为:DSA, 消息摘要的生成用的为SHA-1,分组为28字节一组,内容结构为:摘要 + 分组信息 + 消息 + 签名长度 + 签名
由于加密是对每一组进行加密的。在组中先填充消息摘要等消息。所以可以看到第二段(第一次加密Group1结束)中 在密文第一个字节(-56)前有一段消息摘要等其他消息。解密后生成摘要与签名的摘要进行比对,没有问题。
2 RC4流密码加密实现
2.1 实验环境
语言 : Java
IDE : Eclipse绿色版
2.2 源代码
import java.lang.Integer;
class HomeWork {
publicstatic String MyRC4(String aInput,String aKey)
{
int[] iS = newint[256];
byte[] iK = newbyte[256];
for (int i=0;i<256;i++)
iS[i]=i;
int j = 1;
for (short i= 0;i<256;i++)
{
iK[i]=(byte)aKey.charAt((i % aKey.length()));
}
j=0;
for (int i=0;i<255;i++)
{
j=(j+iS[i]+iK[i]) % 256;
int temp = iS[i];
iS[i]=iS[j];
iS[j]=temp;
}
int i=0;
j=0;
char[] iInputChar = aInput.toCharArray();
char[] iOutputChar = newchar[iInputChar.length];
for(short x = 0;x<iInputChar.length;x++)
{
i = (i+1) % 256;
j = (j+iS[i]) % 256;
int temp = iS[i];
iS[i]=iS[j];
iS[j]=temp;
int t = (iS[i]+(iS[j] % 256)) % 256;
int iY = iS[t];
char iCY = (char)iY;
iOutputChar[x] =(char)( iInputChar[x] ^ iCY) ;
}
returnnew String(iOutputChar);
}
publicstatic String StrToBinstr(String str) {
char[] strChar=str.toCharArray();
String result="";
for(int i=0;i<strChar.length;i++){
result +=Integer.toBinaryString(strChar[i])+ " ";
} return result;
}
publicstaticvoid main(String[] args)
{
String inputStr = "软件学院-白晨-软件22 2121601027";
String key = "loveforever";
String MwB = StrToBinstr(inputStr);
System.out.println("明文二进制流: " + MwB);
// String change = MwB.substring(4, 5);
//String NewMwB=change.replace("1", "0");
String str = MyRC4(inputStr,key);
System.out.println("密文: " + str);
System.out.println("明文: " + MyRC4(str,key));
String str1 = MyRC4("软件学院-白晨-软件22 2122601027", key);
System.out.println("将学号里的“1”改成“2”后的密文:" + str1);
System.out.println("原始密文二进制序列为:" + StrToBinstr(str));
System.out.println("修改后密文二进制序列为:" + StrToBinstr(str1));
}
}
2.3运行结果与分析
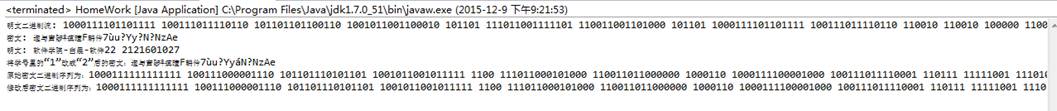
通过实验可以发现,改变明文中的一个字节的数据,只会导致部分密文发生变化,对其他部分没有影响,说明RC4没有雪崩效应。
3 大于3人实现证书生成、签发、通信
3.1 实验环境
平台:Windows 7
实验工具:PGP Desktop 10.0.3
实验人员:李灵杰(lilingjie)、朱鹏宇(zhupengyu)、白晨(baichen)
3.2 实验过程与分析
首先点击 文件—新建PGP密钥 进入下图界面
输入用户名,密码,口令后生成密钥。




导出公钥,使用双方可信任的第三方zhupengyu,给公钥签名并发送给彼此。

将文件lilingjie.txt,用lilingjie的私钥签名,并用baichen的公钥加密,生成lilingjie.txt.pgp文件,传给baichen。



Baichen收到文件后,用自己的私钥解密文件,并用lilingjie的公钥验证签名。

未导入lilingjie的公钥前的仅解密的界面:

导入lilingjie的公钥,解密并验证签名后的界面:

-
网络安全 实验报告
首都经济贸易大学信息学院实验报告实验课程名称网络安全技术首都经济贸易大学信息学院计算机系制实验报告学号实验地点3机房姓名实验时间一…
-
网络安全实验二报告
实验报告20xx20xx学年第1学期课程名称网络安全实验班级10级lt一gt班学号10410901036姓名陈志军任课教师蒲晓川计…
-
网络安全实验报告
网络安全实验学生张守军实验目的1一我要搭建网络安全实验环境配置良好的实验环境时进行网络安全实验的基础工作1VMware虚拟机的安装…
-
网络与信息安全实验报告
中国海洋大学课程名称:网络与信息安全任课教师:学生姓名:学生学号:专业班级:计算机信息保密2010级学院名称:信息科学与工程学院2…
-
网络安全实验报告 模板啊
虚拟机的安装一实验目的1了解虚拟机在构建网络安全实验平台的作用2熟悉虚拟机实验环境的搭建3在VmwareWorkstation虚拟…
-
大工14春《计算机网络实验(一)》实验报告
姓名:张鹏报名编号:C07531xxxxxxxxxxxx0014学习中心:济南奥鹏直属层次:高起专(高起专或专升本)专业:计算机网…
-
计算机网络安全实验总结
计算机网络安全实验本部分主要包括计算机网络操作系统的配置网络扫描网络监听网络入侵1操作系统的安全配置一个好的网络系统配置会有利于计…
- 计算机网络抓包实验报告
- 计算机网络安全实验报告04
-
网络安全实验报告
实验一查阅Linux缺省的存取控制权限实验目的了解Linux文件格式以权限的设置实验环境LinuxCentOS65实验步骤1以ro…
-
网络安全 实验报告
首都经济贸易大学信息学院实验报告实验课程名称网络安全技术首都经济贸易大学信息学院计算机系制实验报告学号实验地点3机房姓名实验时间一…